coverage
Aligning with Industry Standards
Our testing methodologies are baselined against industry testing standards such as OWASP Application Security Verification Standard (ASVS), MITRE Common Weaknesses and Exposure (CWE), and MITRE ATT&CK.
Coverage across the technology stack
Web Applications
Mobile Applications
Native Applications
Cloud Infrastructure
Embedded and IoT
Backend Services
Artificial Intelligence
Drones & Robotics
Industrial Control Systems
approach
Modern testing approaches to meet evolving threats
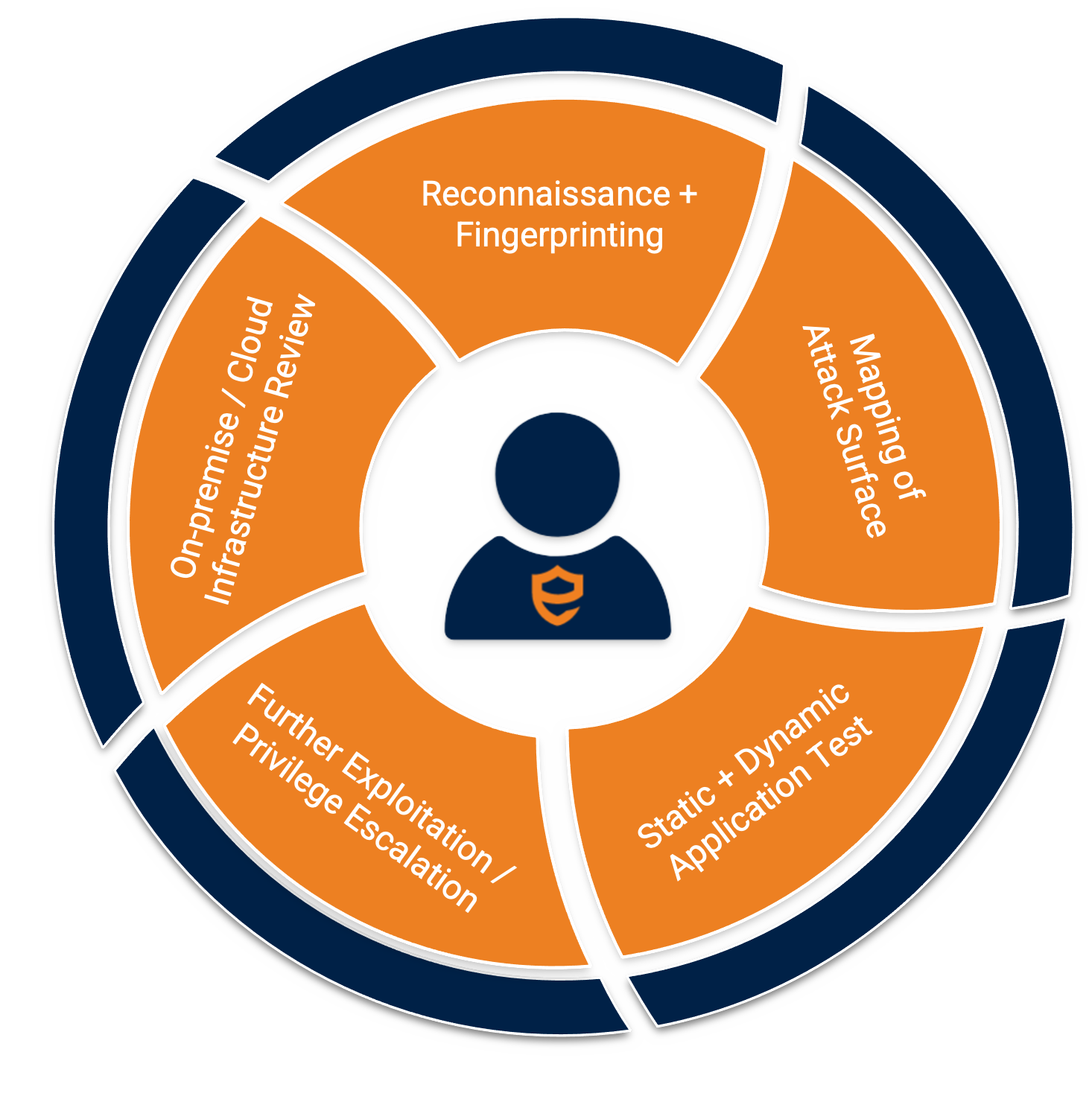
Over the years product security practices have steadily evolved. Through many years of experience, we understand that you may be at varying stage of security maturity and can meet you where we are.
We distinguish ourselves from commoditised security testing services by also performing highly bespoke and thorough security testing. Our security testing projects are carefully tailored to meet requirements and provide tangible outcomes.
We take a systematic approach by dissecting the architecture of the product, consider its unique threat model, then combine offensive research and security engineering skill-sets to simulate likely threat scenarios, carefully assess attack surfaces, and fortify products in a pragmatic manner.
Outcomes
Deliverables
Our customers perform security testing to reduce any security risks that may be introduced by newly acquired or updated software and hardware. Our security assessments will deliver top-tier quality service that works alongside you to get your desired outcomes.
Decades of experience and thousands of security tests later, we are able to remove the unknowns from your environment by pinpointing the exact line of code or configuration where vulnerabilities are introduced.







