 ORM Leaking More Than You Joined For
ORM Leaking More Than You Joined For
By Alex Brown December 18, 2025
A follow-up article in our ORM Leaks series covering newly susceptible ORMs, techniques for bypassing ORM Leak protections, and demonstrating how ORM Leaks can exist in any web application that uses one.
 Gotchas in Email Parsing - Lessons From Jakarta Mail
Gotchas in Email Parsing - Lessons From Jakarta Mail
By Jia Hao Poh November 17, 2025
This writeup goes through the various primitives in Jakarta Mail that could lead to high impact bugs if developers are unaware of the library's quirks. Primitives discussed here here can be applied to other mail parsing libraries.
 New Method to Leverage Unsafe Reflection and Deserialisation to RCE on Rails
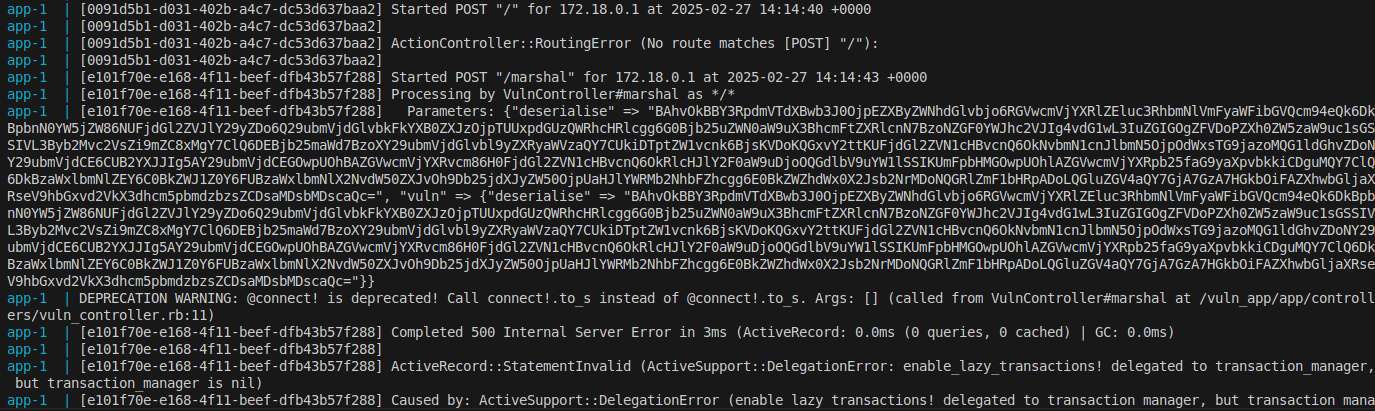
New Method to Leverage Unsafe Reflection and Deserialisation to RCE on Rails
By Alex Brown March 04, 2025
This blog article documents a new unsafe reflection gadget in the sqlite3 gem, that can also be used in a deserialisation gadget chain to achieve RCE and is installed by default in new Rails applications.
 A Monocle on Chronicles
A Monocle on Chronicles
By Matt October 02, 2024
This post provides an overview of Talkback Chronicles for viewing snapshots of trending infosec resources for points in time, and also how to subscribe to a new weekly Newsletter feature.
 DUCTF 2024 ESPecially Secure Boot Writeup
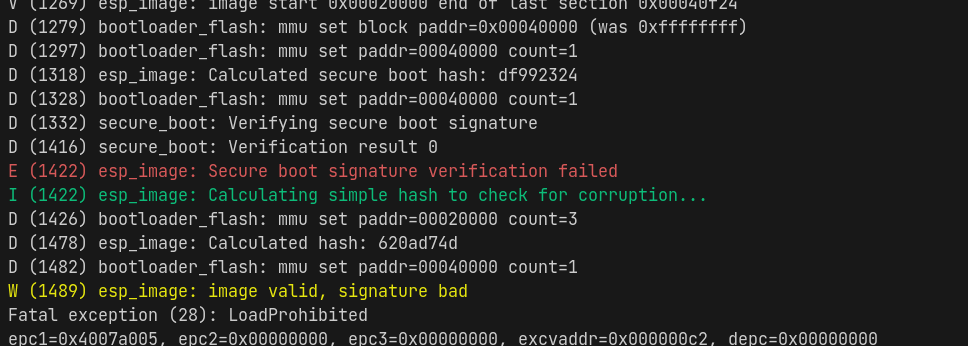
DUCTF 2024 ESPecially Secure Boot Writeup
By daniel August 01, 2024
This blog post covers a DUCTF 2024 pwn challenge called "ESPecially Secure Boot", which required writing an exploit for CVE-2018-18558.
 plORMbing your Prisma ORM with Time-based Attacks
plORMbing your Prisma ORM with Time-based Attacks
By Alex Brown July 08, 2024
Part two of our ORM Leak series about attacking the Prisma ORM and leaking sensitive data in a time-based attack.
 plORMbing your Django ORM
plORMbing your Django ORM
By Alex Brown June 23, 2024
This blog article explains what are ORM Leak vulnerabilities, how they could be exploited to access sensitive information with the Django ORM.
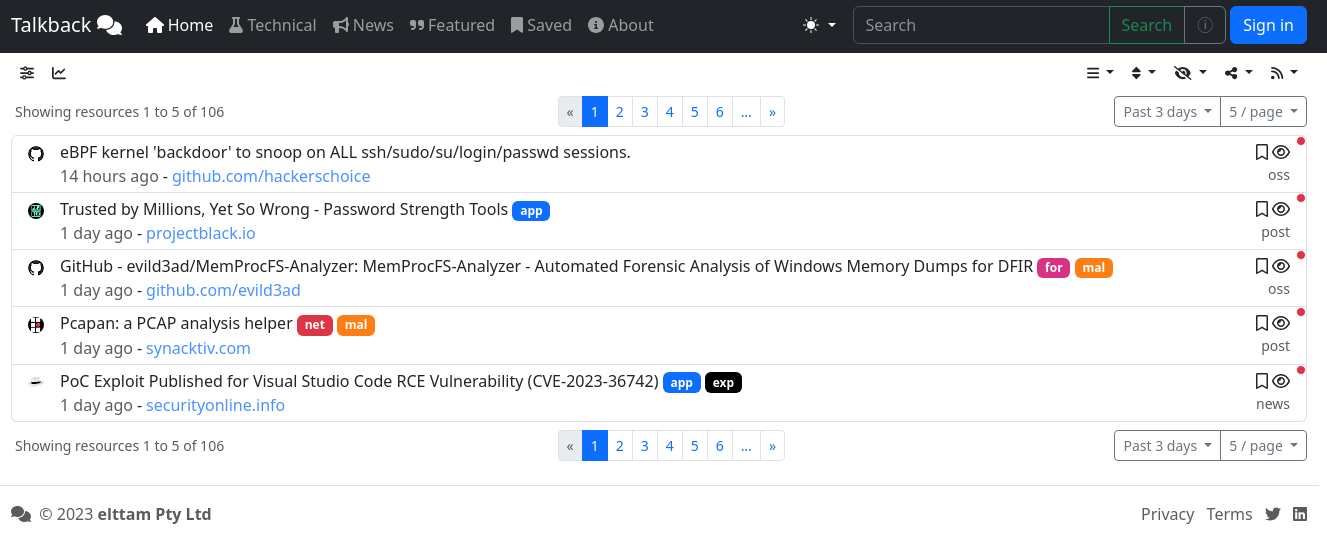 Keeping up with the Pwnses
Keeping up with the Pwnses
By Matt, Seb January 09, 2024
This post provides an overview of Talkback, a smart infosec resource aggregator. The post details how the system works, steps through some of its key features, and also presents how to use the UI and GraphQL API.
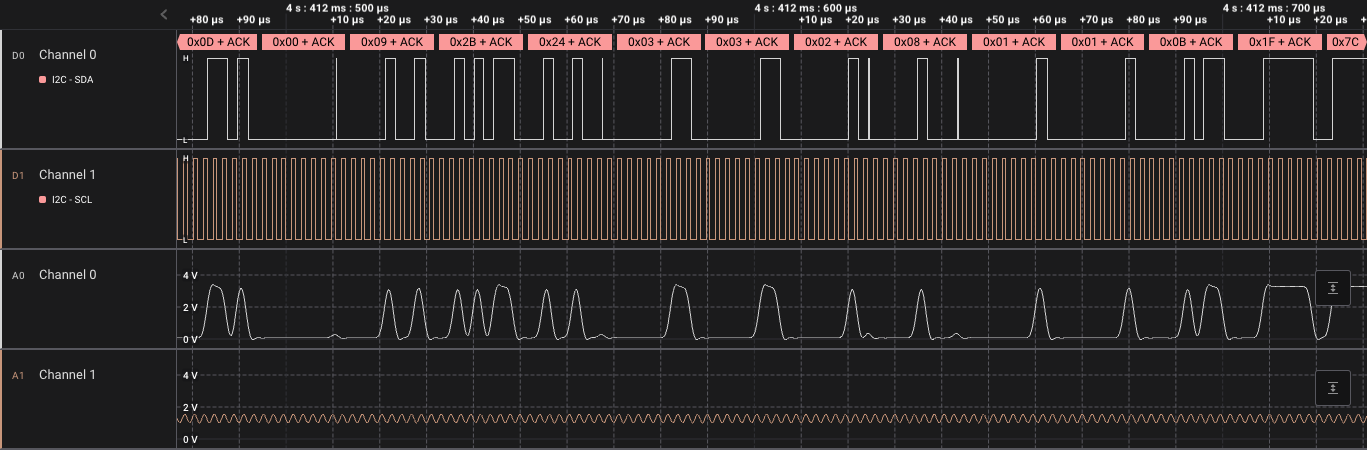 Exploring the STSAFE-A110
Exploring the STSAFE-A110
By Zoltan Madarassy October 03, 2023
Using a sample application, this blog post gives a walkthrough of the I2C communication between the STSAFE-A110 secure element and a host MCU. A tool is released to aid in understanding the I2C flow using a logic analyser.






