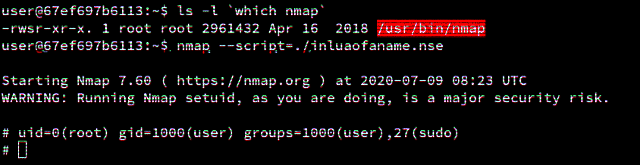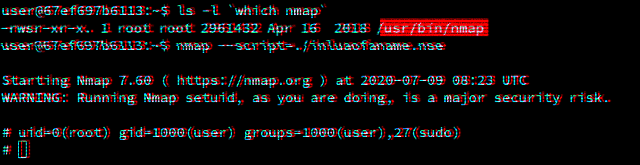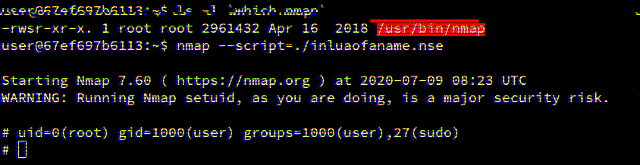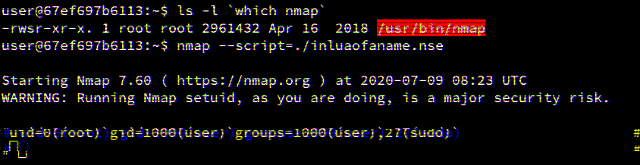
 Lua SUID Shells
Lua SUID Shells
By Brendan Scarvell July 09, 2020
This blog post explores how privileged Lua scripts can pop shells without dropping privileges.
 Hacking with Environment Variables
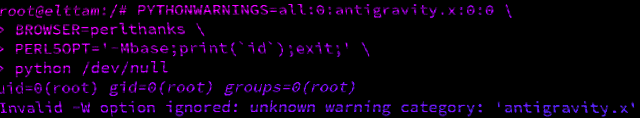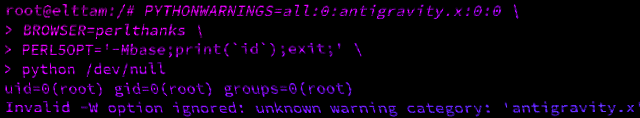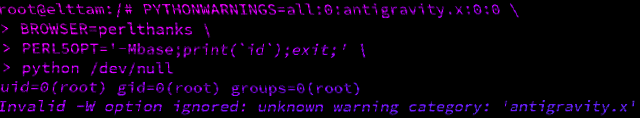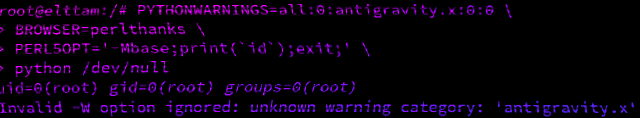
Hacking with Environment Variables
By Luke Jahnke June 24, 2020
A look into how scripting language interpreters can execute arbitrary commands when supplied with malicious environment variables.
 Are you winning if you're pinning?
Are you winning if you're pinning?
By Mykel Pritchard January 24, 2019
This blog post takes a brief look at TLS and certificate pinning, the problem of trust in Certificate Authorities that pinning attempts to address, and discusses whether the lack of certificate pinning in a mobile application constitutes a vulnerability.
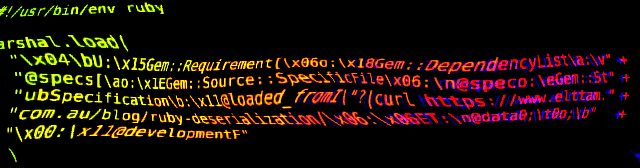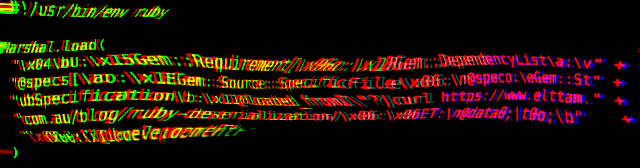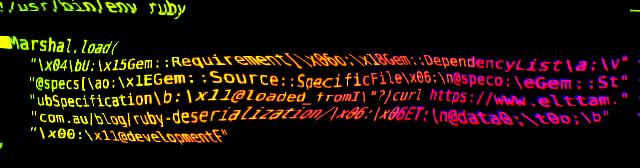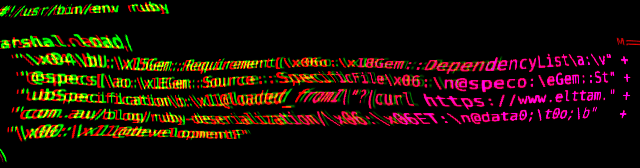 Ruby 2.x Universal RCE Deserialization Gadget Chain
Ruby 2.x Universal RCE Deserialization Gadget Chain
By Luke Jahnke November 08, 2018
This blog post details exploitation of arbitrary deserialization for the Ruby programming language and releases the first public universal gadget chain to achieve arbitrary command execution for Ruby 2.x.
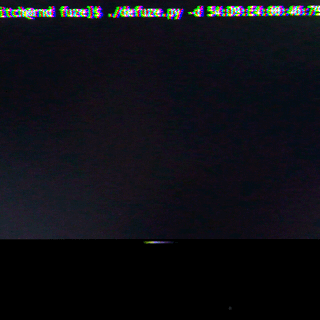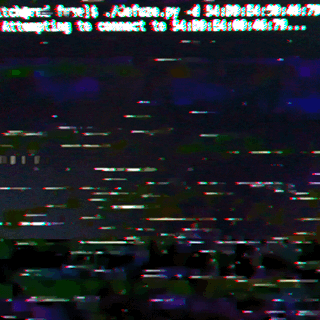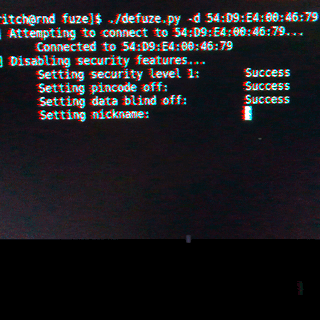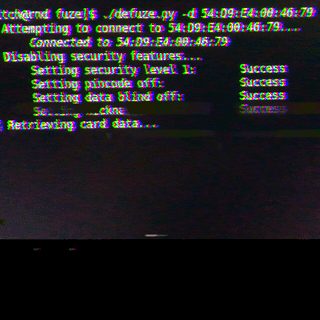 Fuze Multi-Card Technology Security Review
Fuze Multi-Card Technology Security Review
By Mykel Pritchard April 24, 2018
Reviewing the security of the Fuze card device revealed no trust boundary between the card and the connecting device, which allowed complete access to the Fuze card's settings and stored credit-card information.
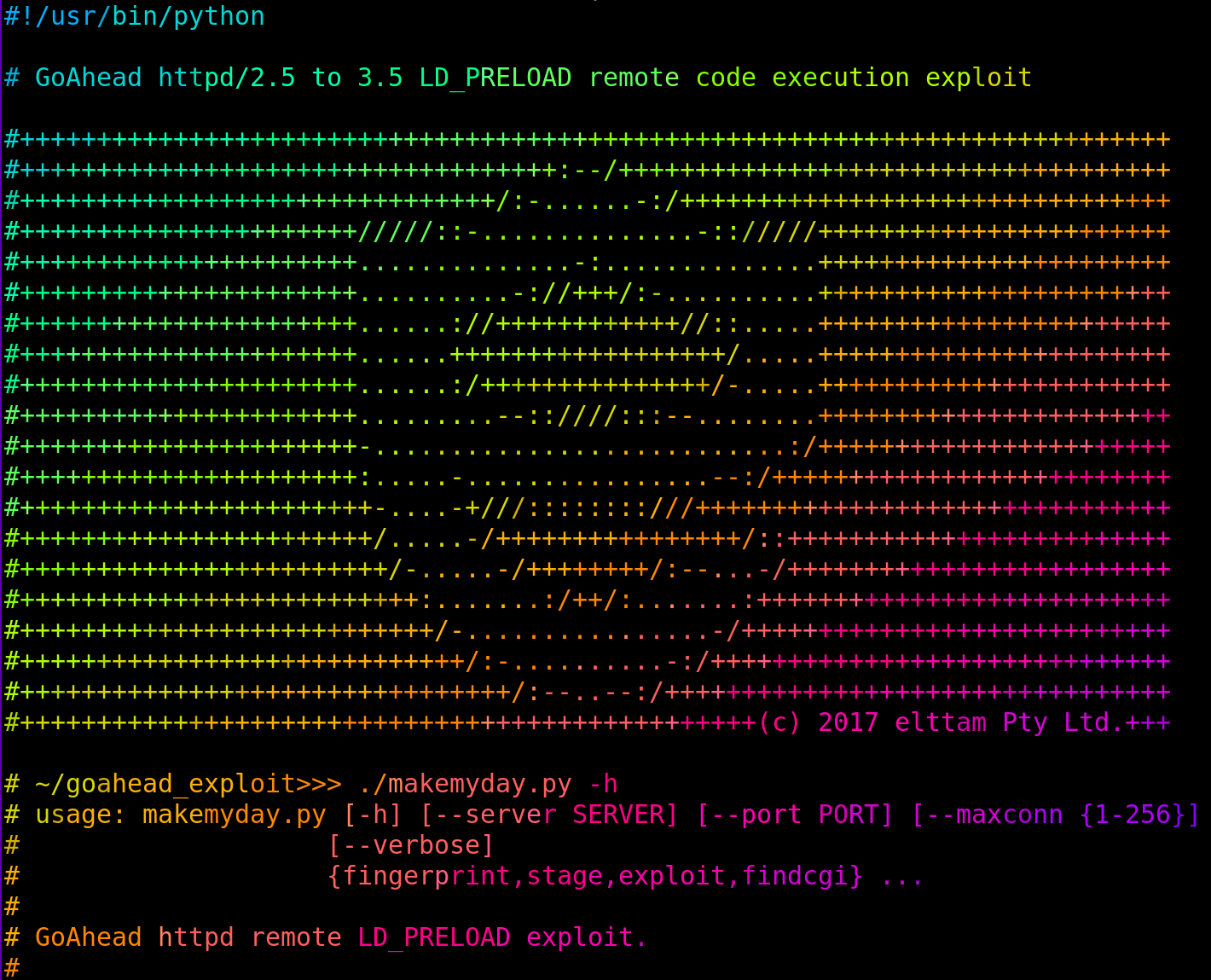 Remote LD_PRELOAD Exploitation
Remote LD_PRELOAD Exploitation
By dan December 18, 2017
Analysing a vulnerability in all versions of the GoAhead web server < 3.6.5 that allowed for reliable remote code execution via LD_PRELOAD injection.
 Building Hardened Docker Images from Scratch with Kubler
Building Hardened Docker Images from Scratch with Kubler
By berne November 16, 2017
How to use Kubler to build hardened, minimalistic, Docker Images from scratch for better security
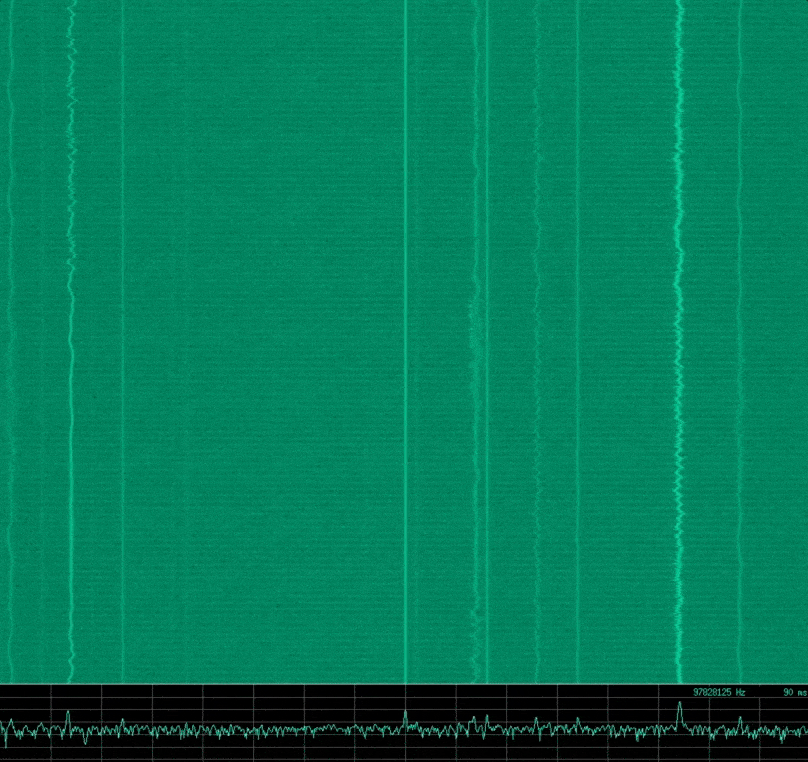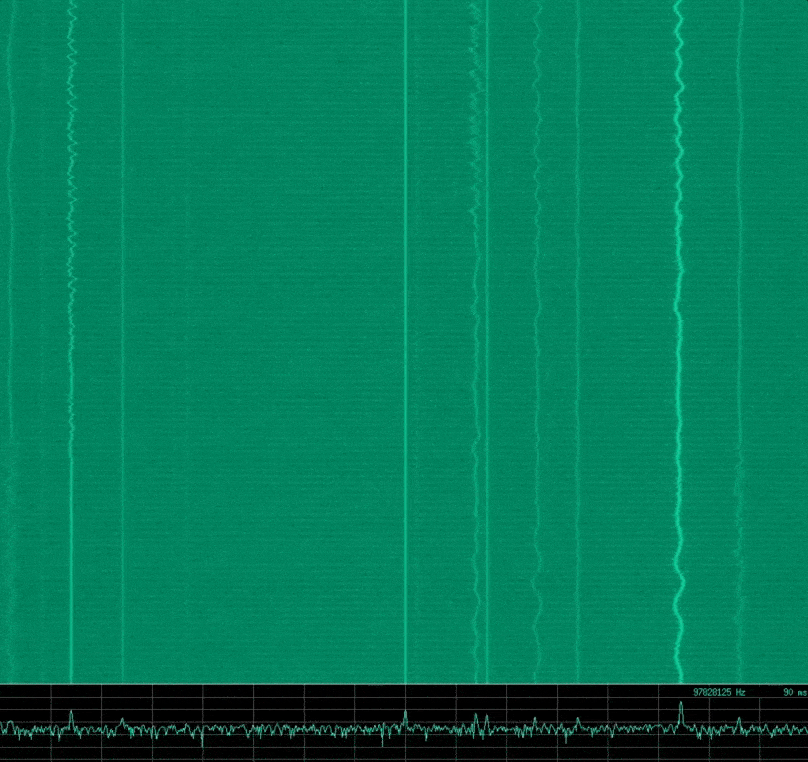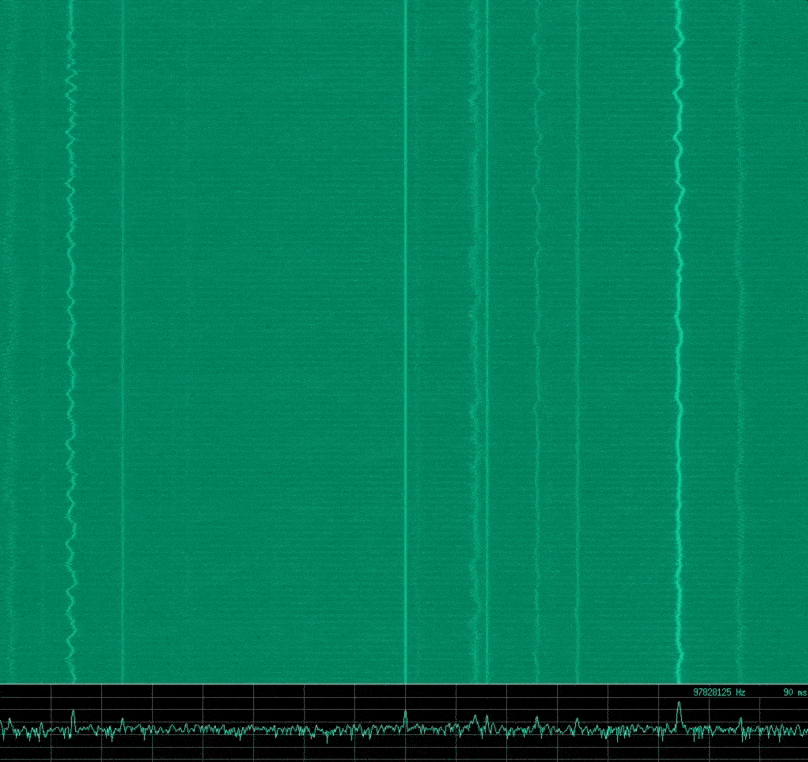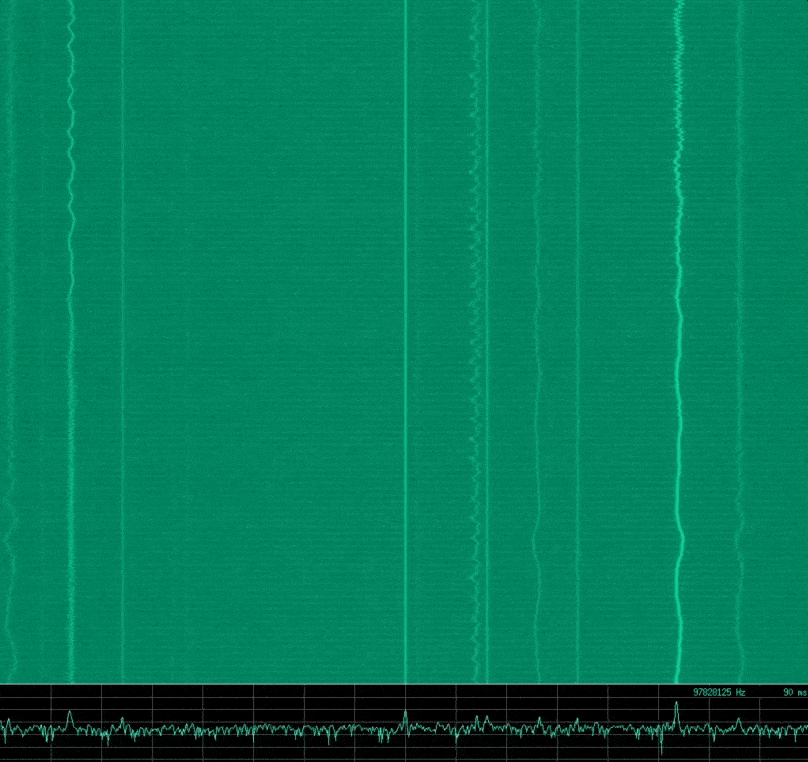 Intro to SDR and RF Signal Analysis
Intro to SDR and RF Signal Analysis
By Mykel Pritchard June 15, 2017
We take a brief look into Radio Frequency (RF) theory, Software Defined Radio (SDR), and visual analysis of various RF signal characteristics. We discover a good methodology for reversing RF signals, along with some simple analysis of some common RF remote devices that might be found around the home.
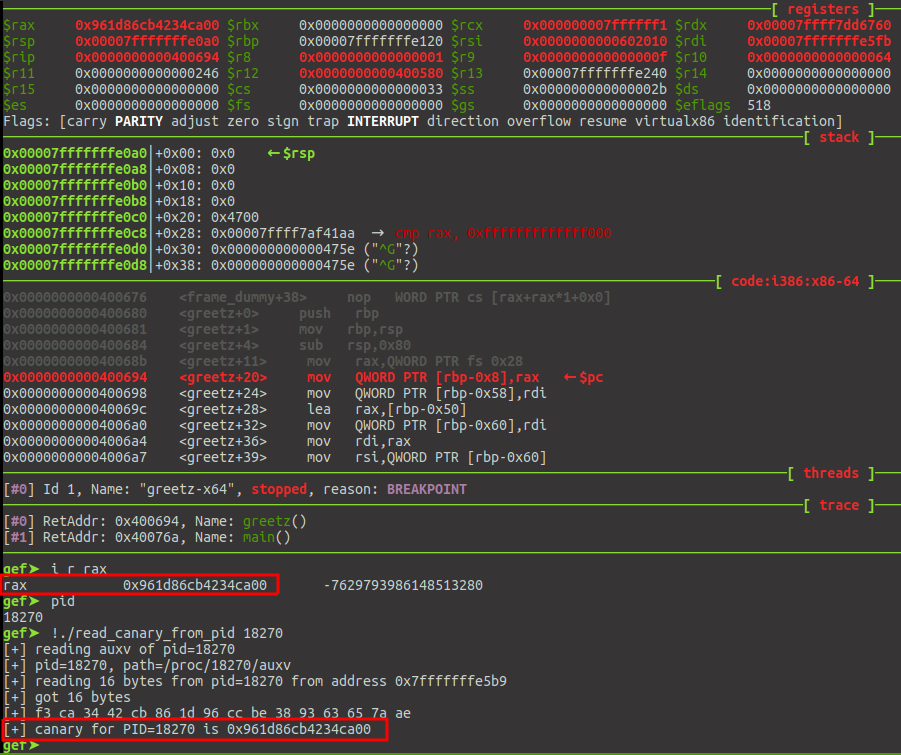 Playing with canaries
Playing with canaries
By hugsy January 24, 2017
Analysis of compiler stack canaries and their implementation across various architectures.






