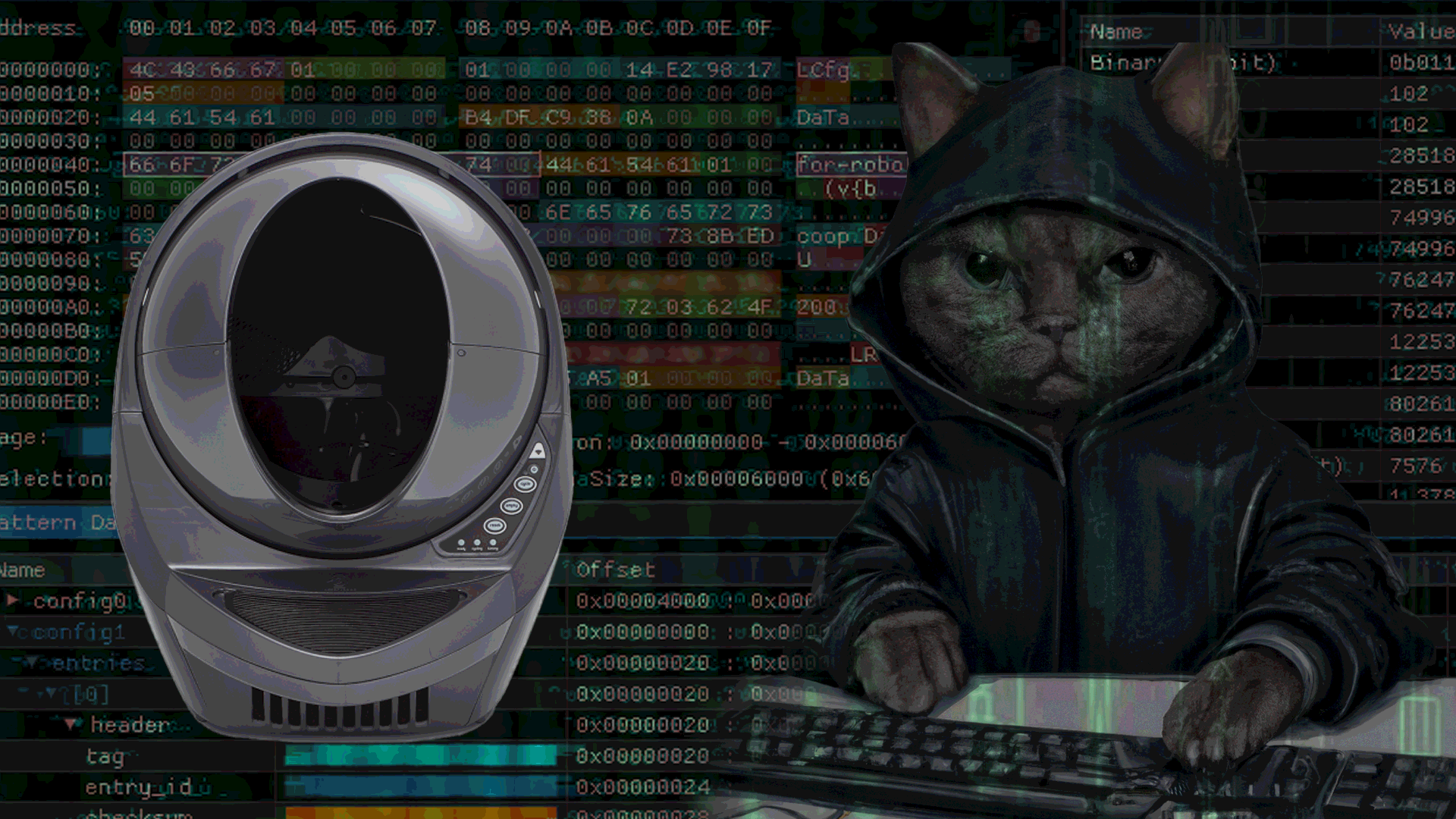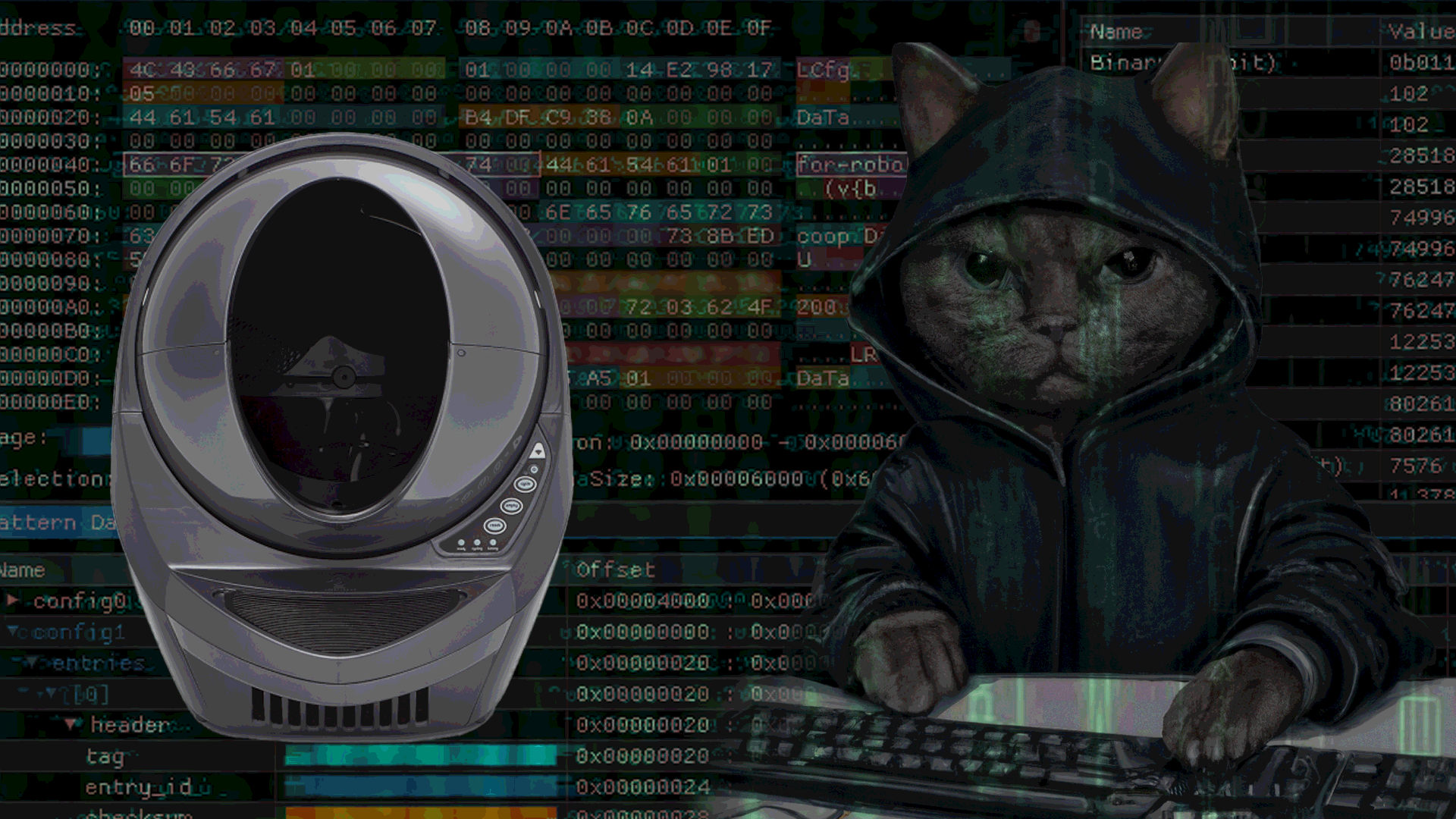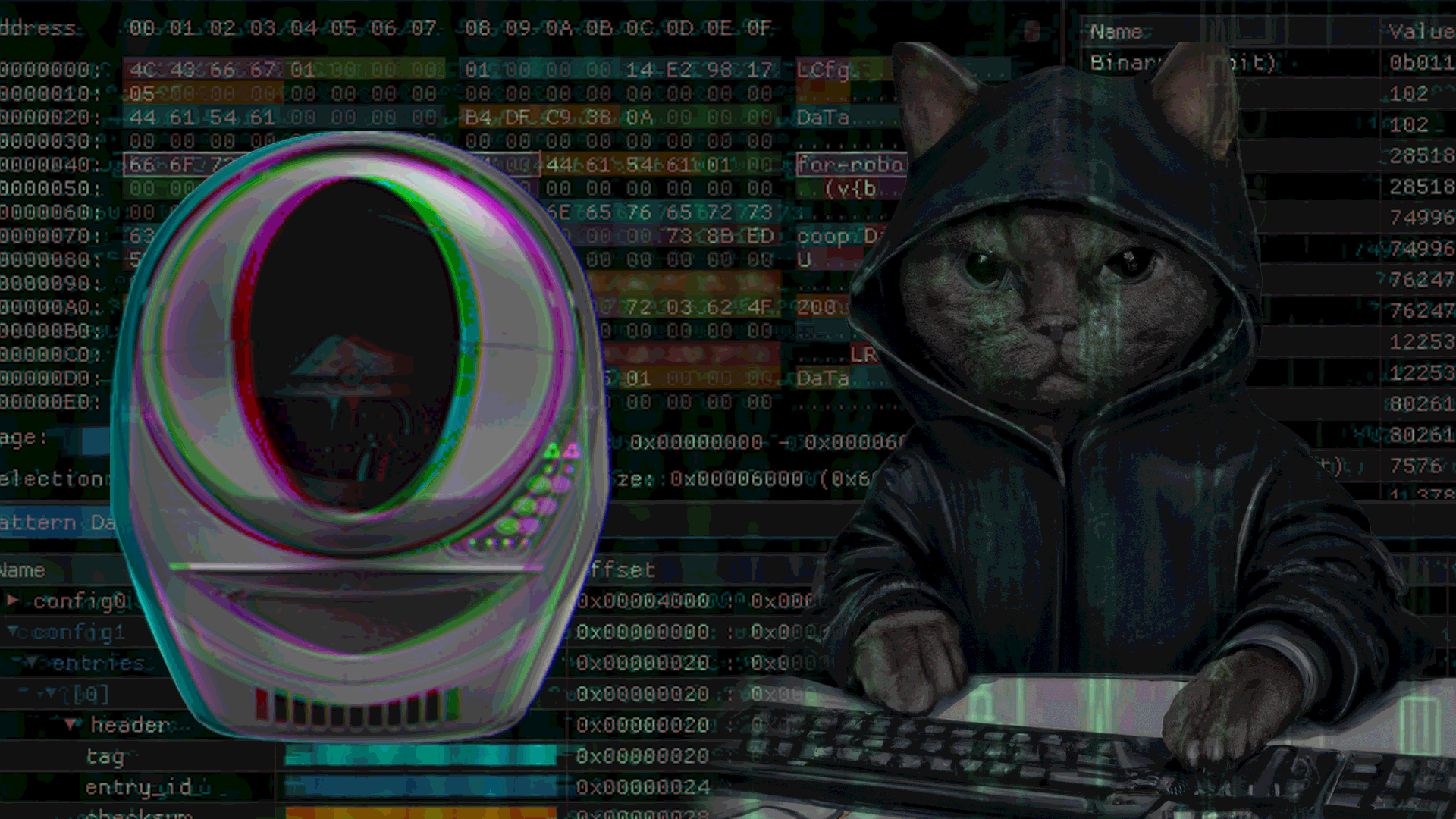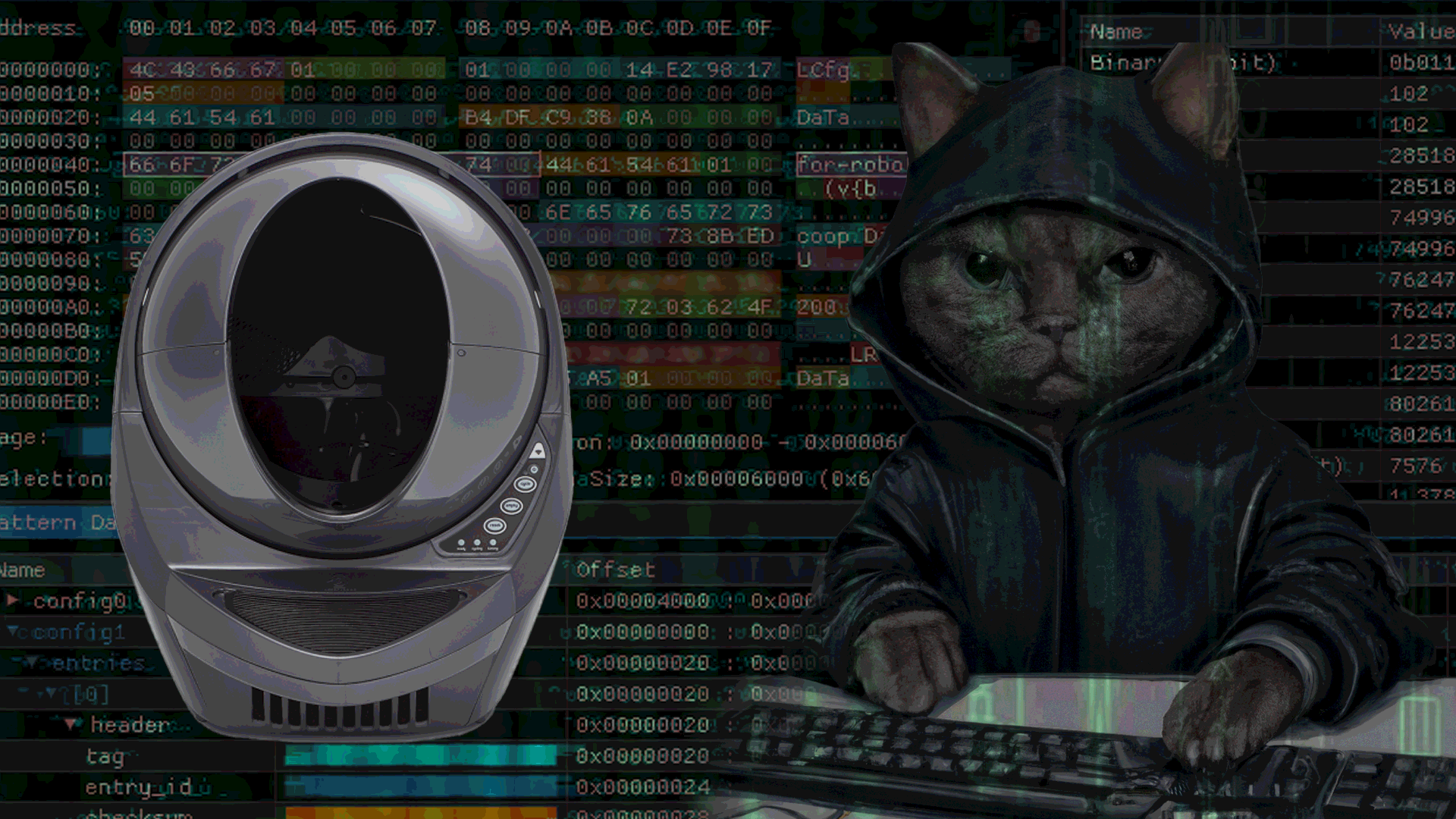
 RE of LR3
RE of LR3
By Victor Kahan September 06, 2023
This blog post provides a walk-through of ESP32 firmware extraction and analysis to understand the technical implementation of the Litter Robot 3.
 Abusing Amazon VPC CNI plugin for Kubernetes
Abusing Amazon VPC CNI plugin for Kubernetes
By berne July 17, 2023
This blog post covers exploring the Amazon VPC CNI plugin for Kubernetes, and how it can be abused to manipulate networking to expose access to other resources, including in other VPCs.
 PwnAssistant - Controlling /home's via a Home Assistant RCE
PwnAssistant - Controlling /home's via a Home Assistant RCE
By elttam May 09, 2023
This blog post provides a summary of the Home Assistant architecture, attack surface, and our approach auditing pre-authentication components. This post summarises and links to a few published advisories, including a Critical pre-authentication vulnerability.
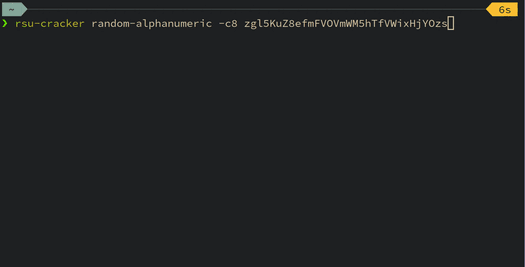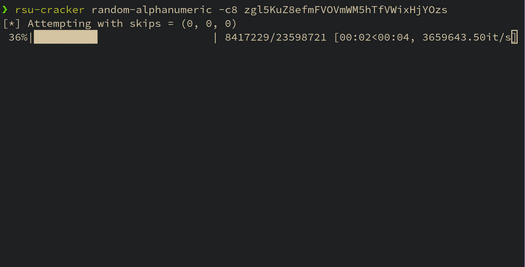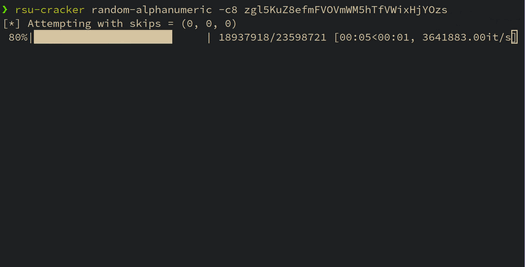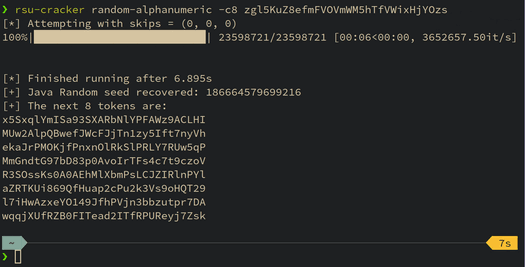 Cracking the Odd Case of Randomness in Java
Cracking the Odd Case of Randomness in Java
By joseph February 09, 2023
This blog post details a technique for breaking Apache Commons Lang's RandomStringUtils and Java's random.nextInt(bound) when the bound is odd. A tool is released which demonstrates the practicality of the attack.
 Golang code review notes
Golang code review notes
By Zoltan Madarassy June 30, 2022
This blog post is aimed to help people performing security code reviews on Golang code bases to identify dangerous code patterns.
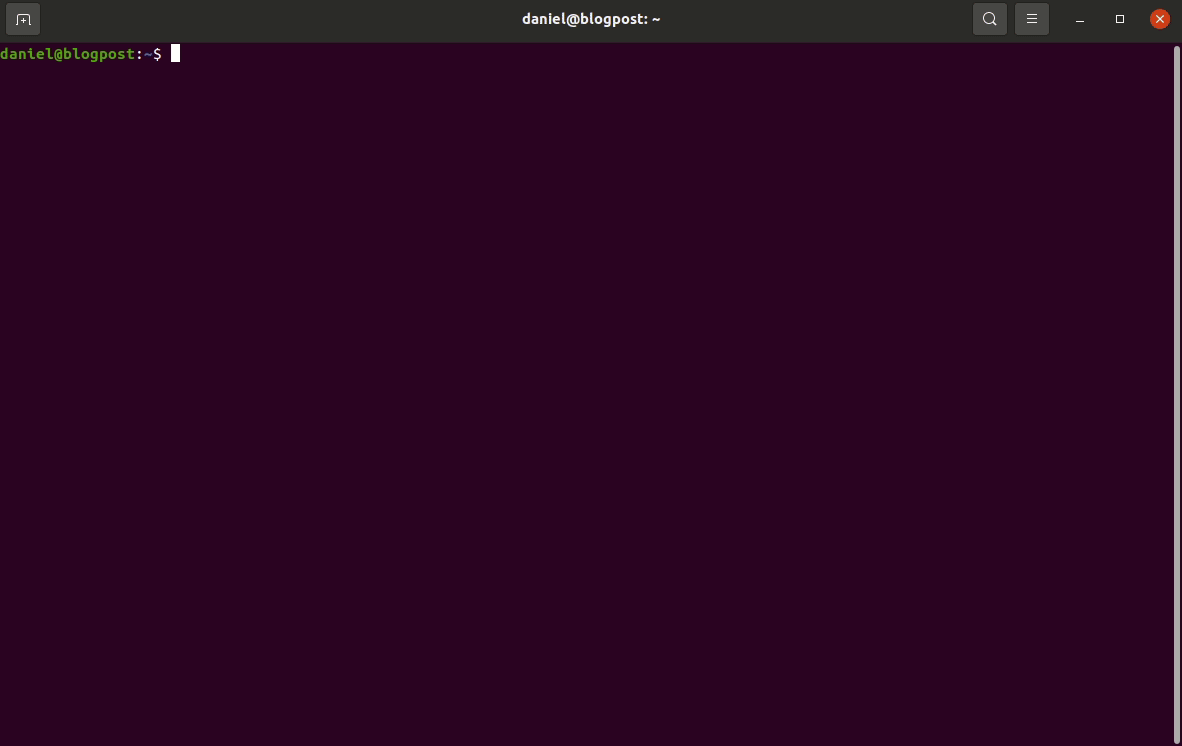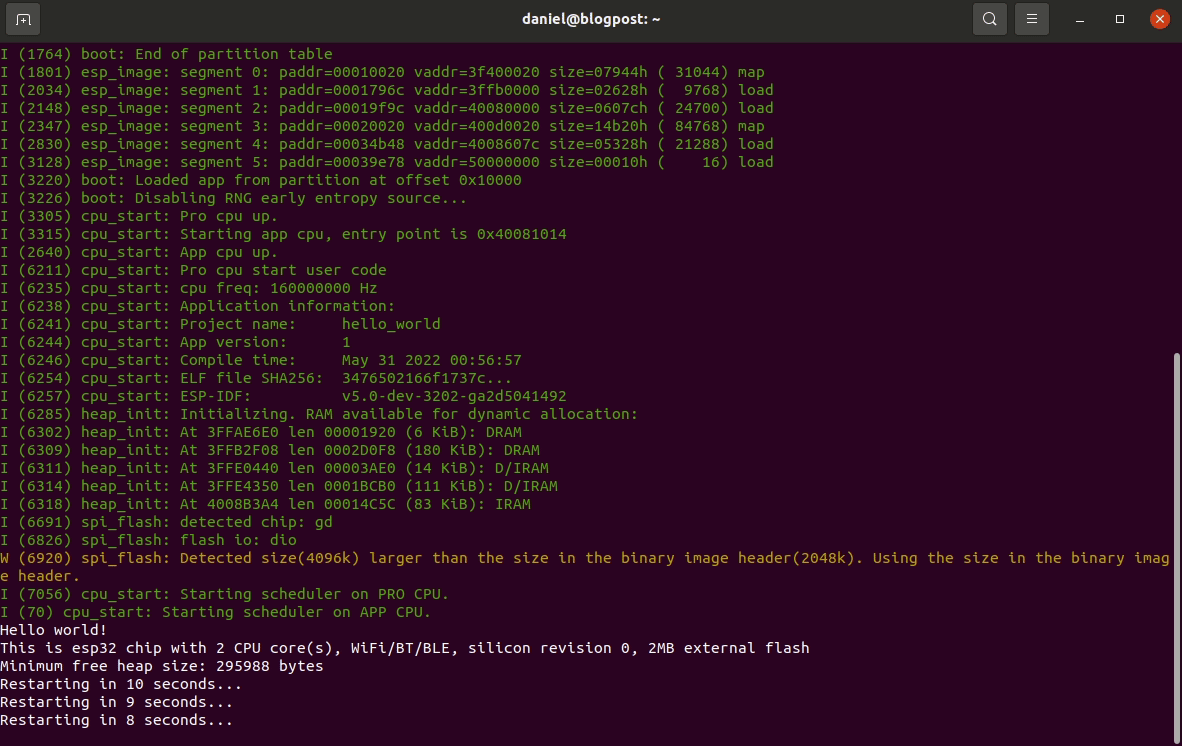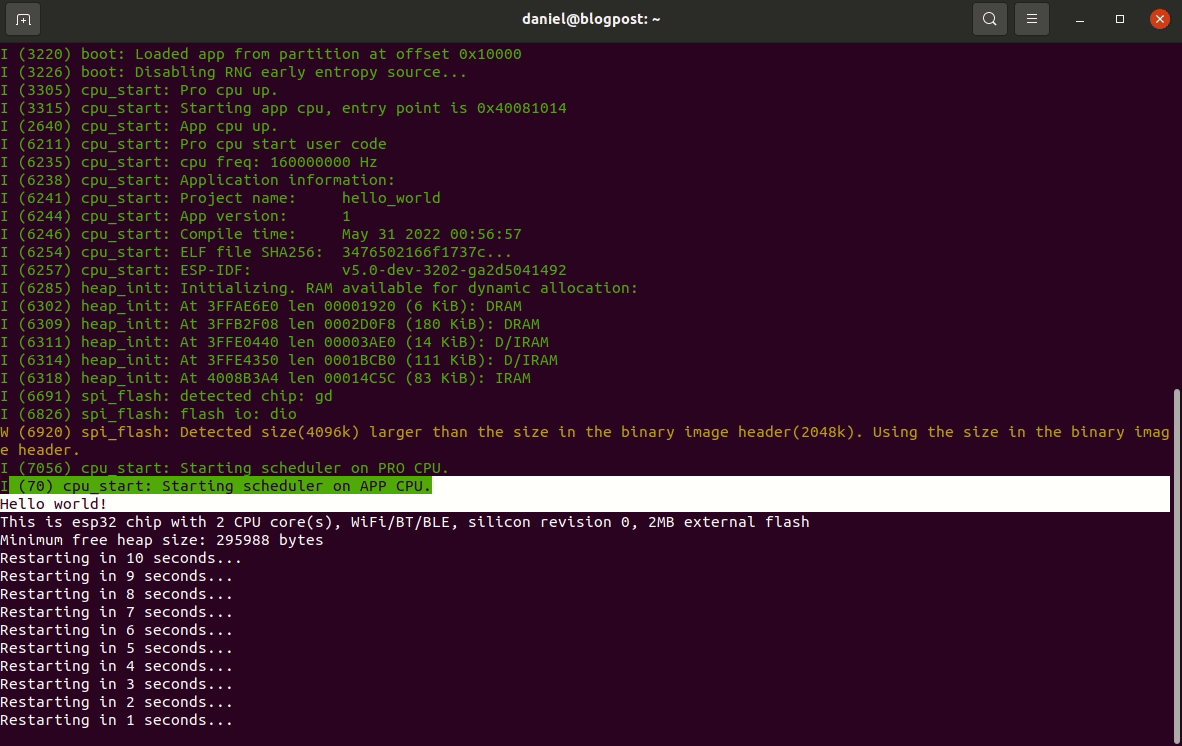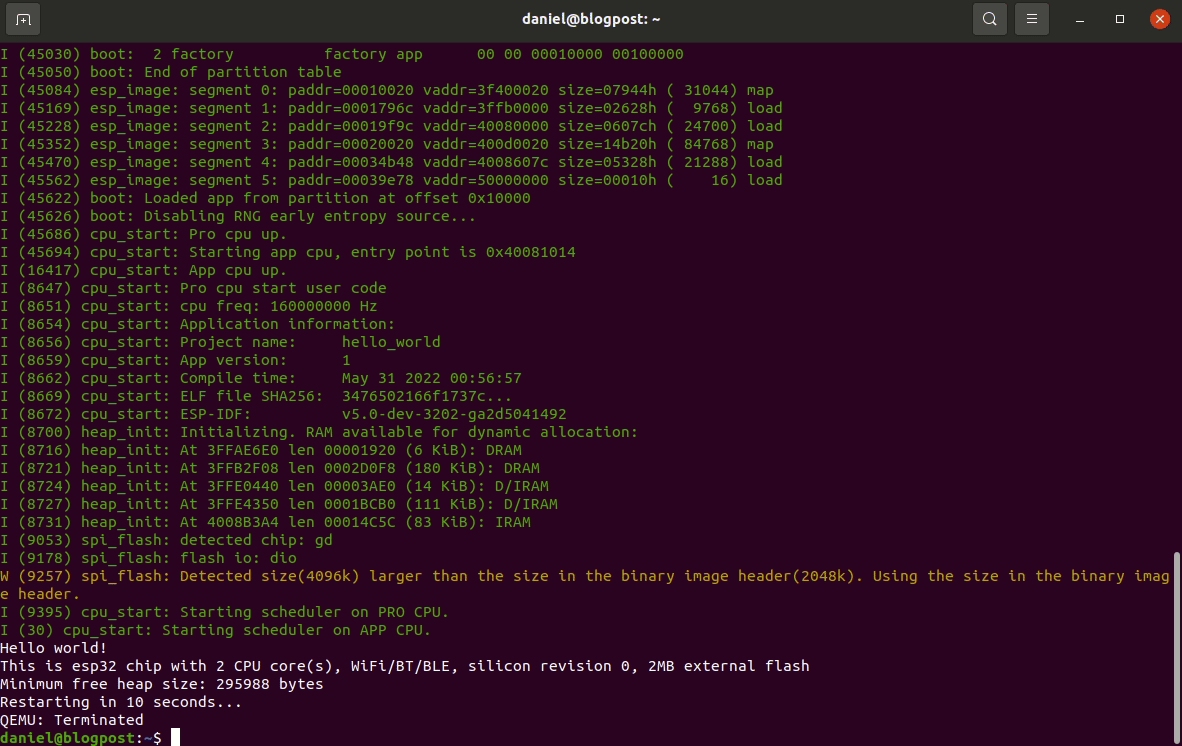 ESP-IDF setup guide
ESP-IDF setup guide
By Daniel Hodson June 06, 2022
This post is for vulnerability researchers looking at the ESP32 and would like a quick setup guide.
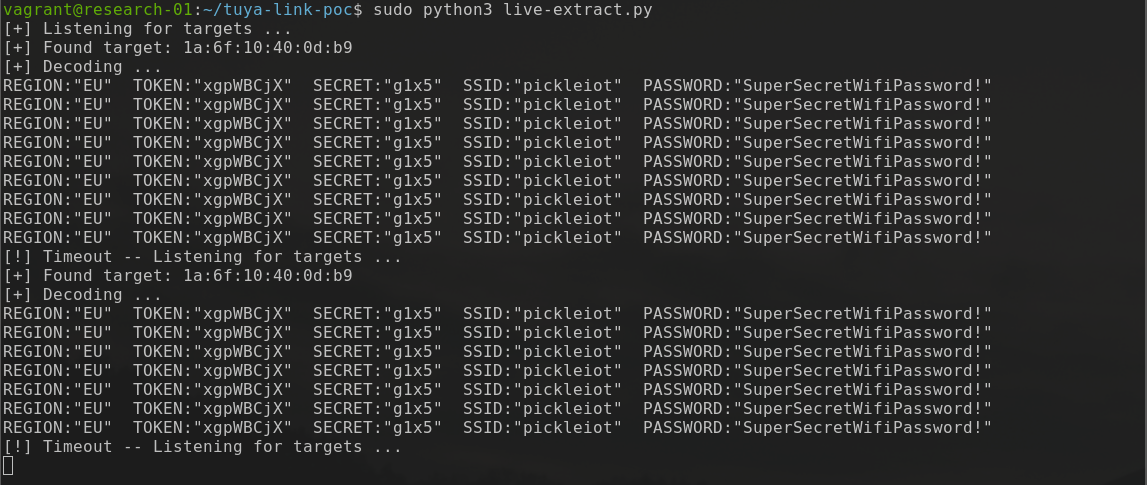 Tuya IoT and EZ Mode Pairing
Tuya IoT and EZ Mode Pairing
By Mykel Pritchard December 09, 2020
This blog post aims to highlight how EZ mode pairing implemented by Mirabella Genio and other Tuya Cloud IoT devices broadcast your WiFi credentials to the neighbourhood.
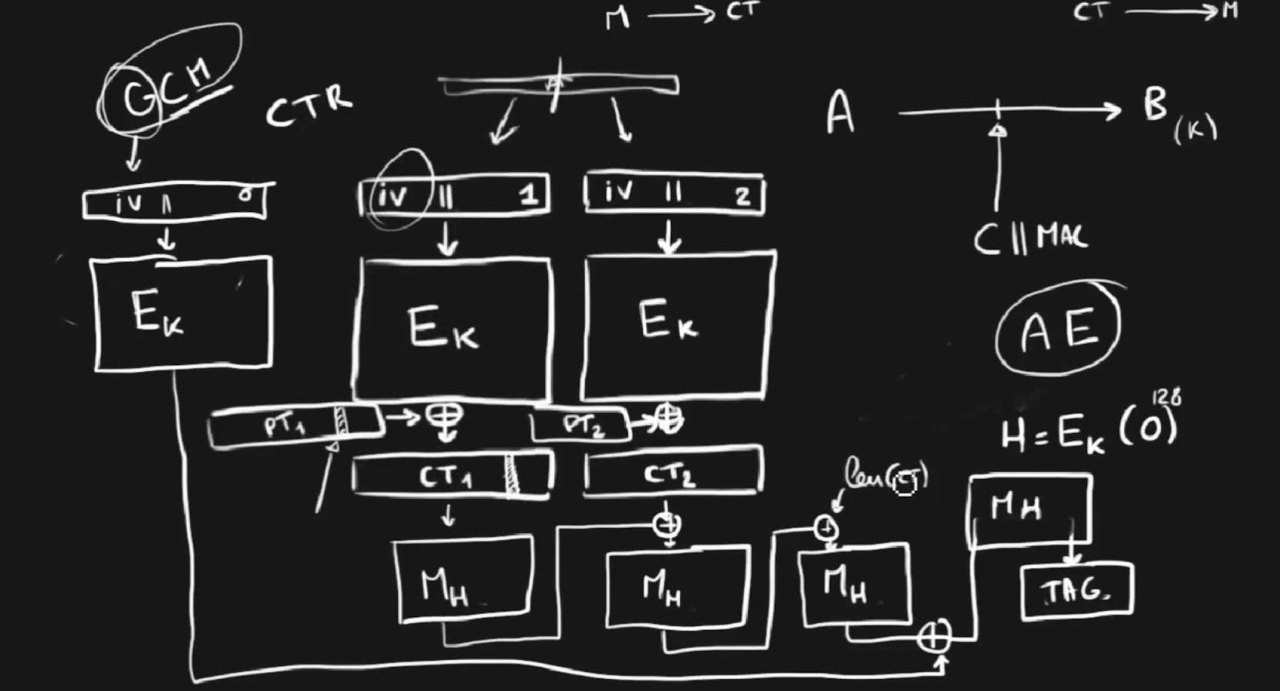 Attacks on GCM with Repeated Nonces
Attacks on GCM with Repeated Nonces
By Sebastien Macke September 25, 2020
This blog post illustrates the security consequences of nonce-reuse in AES-GCM with a Proof of Concept exploit on a vulnerable demo application
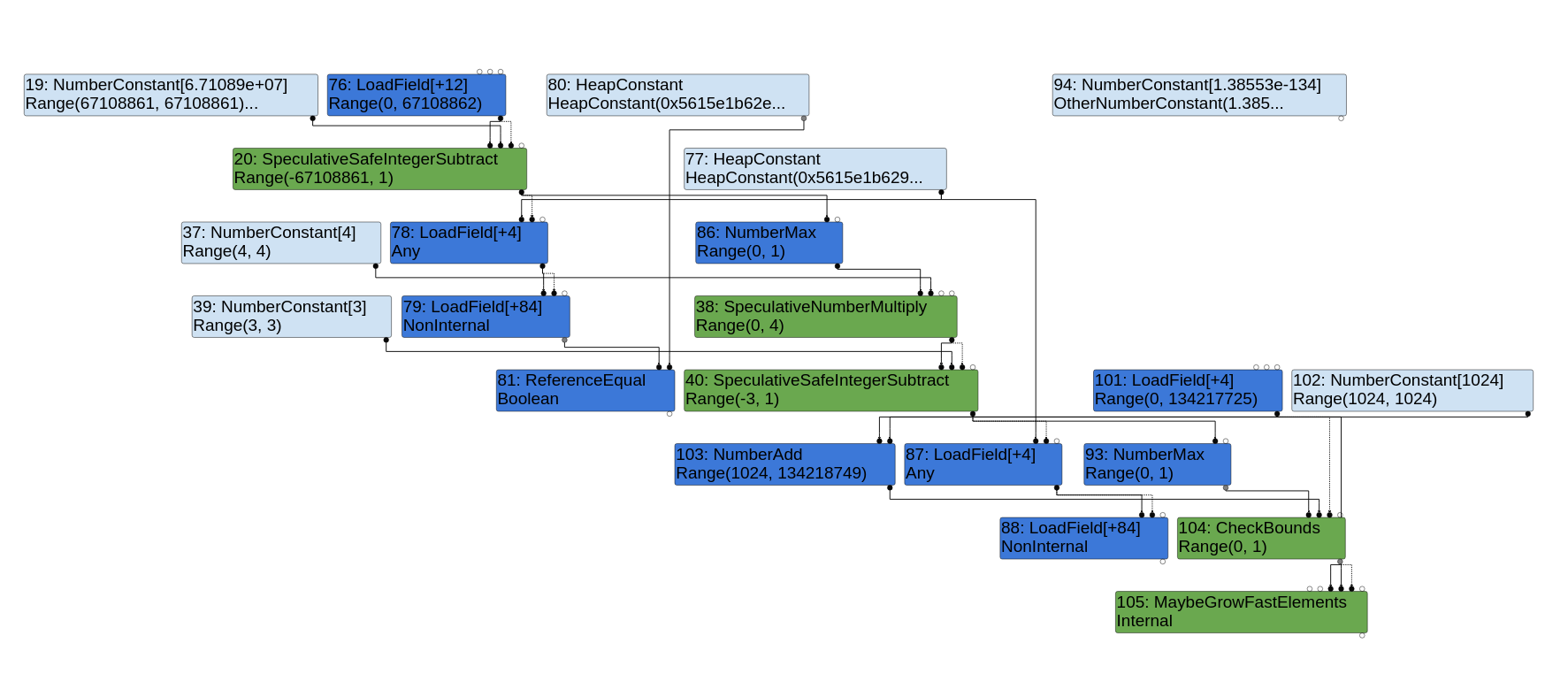 Simple Bugs With Complex Exploits
Simple Bugs With Complex Exploits
By Faraz September 03, 2020
This blog post details a root cause analysis for Project Zero Issue 2046 found by Sergey Glazunov.






